Notorious Internet Fraudulence and Ways to Avoid Them
The Internet plays a huge role in our lives. With the emergence of technology business owners as well as customers are facing numerous incidents of fraudulence and business are getting affected for this notorious practice. If you are running a business or a regular customer of online business, you must know various types of scamming take place now and then. If you’ve already witnessed a case on the internet and if not, you must be aware of all the scams and take necessary steps accordingly. The increasing digital extortion is shaping as a bigger threat than online fraud.
Phishing
As the name suggests, it is a practice to fish sensitive information from people online. It can create a nightmarish situation that you should avoid in every situation to come. It is the most common scam operation on the internet. This type of scammers motivate you to provide all valuable information starting from valuable data, passwords, date of birth, card details for identity verification in the name of protecting you from any fraudulence, however, they are committing the same. If you want to make sure that you are in a genuine site, check that the website address has an https:// address. The fake fishing site usually starts with http:// without the ‘s’. if your valuable information falls into wrong hands, it would ruin all your secured information and money.
Malware
It is another prevalent form of online fraud is the malware attack. It is malicious software, that means, they are infectious files, potentially harmful to a computer or a site. It could lead to serious loss of business and reputation for the webmasters. Malware could be infused by exploiting a vulnerability on a website. The most common ways a hacker injects malware are SQLi, JavaScript, code injection.
Credit Card Hacks/ Credit Card loan

Hackers replace the original form with the phishing form to collect customer’s confidential information and expose it on the black market. Sometimes the payment method is interrupted and corrupted. The payment by the customers does not reach to the sellers with the process of manipulation. One significant disadvantage of this hack is the sellers remain clueless until anybody reports to him.
Sometimes you receive emails from different websites stating that they are interested to give you an additional loan in a very low-interest rate. This scam is believable because some credit card companies often offer such loan schemes and charges fee for their service, but a legitimate company would only provide you credit loan in exchange of annual fee after you receive the credit card. Sometimes the offers are very tempting.
The Nigerian Scam
Sometimes, we receive messages from Nigerian, stating that, they belong to a royal and wealthy family and in search of assistance to aid then to get their inheritance outside their indigenous nation so that they can make a substantial donation for any charity. Many people fall trap in their story and send them money to cover non-existent expenses. There is a variety of way to approach people and trap them.
Lottery Scam
I think all of us, has received email frequently informing that, you have won a lottery of millions. They will ask you to deposit some money to avail your prize money. Then you will realize you have never bought a lottery ticket like that. Once you deposit the money, you will never be going to get it back. This is how you will fall in a trap. So next time, when you receive such mail, be aware. Because no genuine lottery scan asks for prior payment from the winner. This is a witty way to extort money from you.
Overpayment Scam
the scam involves expensive items like a car, where the scammers offer to pay you more. They try to make it authentic by releasing real money order. When you deposit it in your bank, they ask you to release the vehicle and the cash for the difference. This scam is quite convincing as it involves real money order, that is not at all authentic. The money order is not authorised, though it looks like genuine. Eventually, you will be left without a vehicle and with less cash, that you had before the transaction.
Career Opportunities
Scammers keep track on your browser history, your resume to catch their next victim. You may receive an employment offer for international companies or any other coveted deal. They generally offer post like a financial representative. In exchange of labour, they offer you commission and finally when you provide them with your bank account details to receive the payment. This way when they have complete access to your identity and bank details, they commit what they aimed for.
Donation
Some of our’s integrity tell us to donate when we come across such organisations who collect charitable fund. Scammers take the advantages of such people and them in turn fall in the trap. They set up fake websites to collect donation which you are contributing for a noble purpose. So, when you are not sure about a website or probably visiting it for the first time, make sure it is authentic, ring up directly the organisation. Be careful before you go for online payment.
Pyramid Scheme
in this scamming process, the scammers will reach you through emails. Once you sign up to your email, your money will be parted. Do not participate in any online contest where you are asked to provide your login details. Do not get tempted by the offers. Pyramid schemes are unsustainable and illegal.
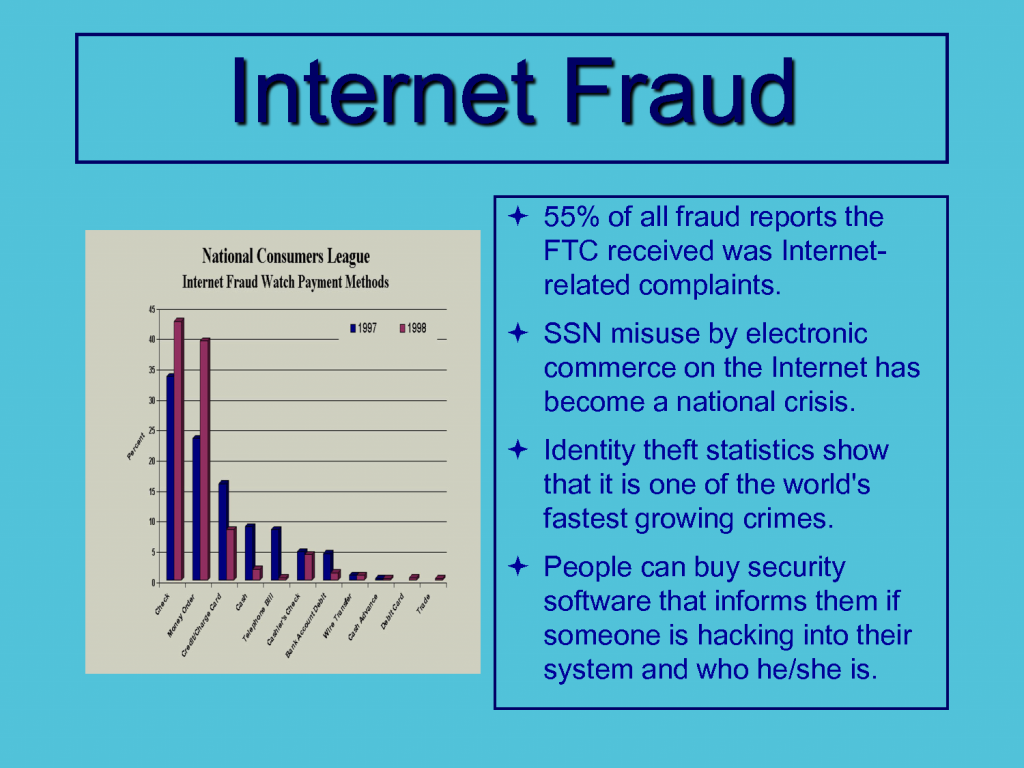
Cybercriminals have developed increasingly advanced technologies in the last few years. They are hampering the security of internet users. The average crime has grown up to 50 percent. Cyber Attacks are getting more sophisticated nowadays due to the invention of new technologies. Almost 48 percent of total mobile users do not use any security software. Most of the users do not take the most basic security steps. In the United States, the direct cost of global online fraud has reached up to $113 billion.
According to a recent report, given by Cisco:
The basic focus of these types of a threat does not target sites for gambling, pornography or pharmaceutical websites. The threat basically comes from authorised websites. Search engines are more malicious prone than fake software sites. The officer of Global Government and Corporate Security for Cisco, “Today we live a blended work-personal life. The hackers know this. The security threats that we encounter online like embedded web malware while visiting popular destinations like search engines, retailers, social media sites and smartphone/tablet apps no longer threaten only the individual; they threaten our organizations by default.”
Be more private on internet
Nowadays people tend to post everything on the internet. It is very easy to track a person through their social media posts. Your lifestyle, standard of living, etc get reflected on their social media profile. Hackers or scammers could easily target you as you have already provided 80 percent of your valuable information. They could take advantage of this and utilise that information to hit their target. Therefore, keep your social media profile private, so that everyone could not trace your activity and set their next target.
Change important passwords often
If you want to save your website from getting hacked, or if you want to protect the security of your account, make a strong password that is hard to track. Create a unique password comprises of upper and lower case letters, symbols, numbers, etc. Not only that you need to change the password very often. This process is known as a brute force in cybersecurity.
Update software/websites when needed
People tend to overlook the simple task of updating the software. If you always update to the latest versions of an application, they would reduce the risks of it to get hacked. Using the outdated version of a software, website, plugin, the theme can enhance the chances of getting exploited. Always stay updated with the latest version of the application.
Use Security solution

solidifying your website with proper security software is one of the fundamentals you should follow to safeguard your websites. You can take an example like Astra’s web application firewall provide you with comprehensive protection to your website and take you one step closer to security. It protects you from SQLi, XSS, OWASP, CSRF and other major threats. It works for monitoring the website full-fledged and manages the dashboard.
solidifying your website with proper security software is one of the fundamentals you should follow to safeguard your websites. You can take an example like Astra’s web application firewall provide you with comprehensive protection to your website and take you one step closer to security. It protects you from SQLi, XSS, OWASP, CSRF and other major threats. It works for monitoring the website full-fledged and manages the dashboard.
DoS Attack (Denial of Service)

Though it is not directly related to scamming, it is a notorious practice of hackers to slow down your website. DoS attack denies legitimate users to access your request or making it extremely slow. This type of attack is implemented by hitting the target resources with too many requests at the same time. As a result, this effect can either crash the servers or slow it down.
DDoS Attacks (Distributed Denial of Service)
This is one of the most common forms of digital extortion and it been a growing trend. A recent study has suggested that 41 percent of organisations around the world had been affected by the DDoS attack. Businesses that solely depend on online can have a disastrous effect through extortion. The worst part is many organisations do not report after witnessing these types of attacks because of their reputation or fearing that their customer would assume their own security is under threat.
Data Theft
Holding secured data for threatening business organisations in another common form of digital extortion. In the year 1014, Domino’s Pizza got affected significantly when the hackers threatened to expose valuable information of 6,00000 customers in exchange for a good ransom. It can lead to disastrous consequences for your business. In the case of corporate business, a similar situation may arise where corporate secrets are under threat, which eventually may lead to damaging effects in your company.
Sextortion
It is referred to a form of blackmail where sexual information or images are used to extort favours from victims. In this crime, men are being targeted and lured to engage in sexual conversation and then get intimated through videos and chats. This scamming process finally ends up with exposing themselves. Eventually, criminal demands and threatens are made in exchange for a huge amount of money.
Another kind of sextortion involves damaging your device with an infected virus and then snatching valuable information and sometimes intimate photos are collected to threaten the user. The most negative disadvantage of this scam is when you fall victim after involving in such a notorious scam you hesitate to take a legal step.
Ransomware
It is a type of malware from cryptovirology which threatens to bring out the data and block the access permanently. It can affect either an individual or an organisation. It corrupts and infects files and documents of a computer system, either by encrypting or by locking the system. And then, a ransom is demanded to free the system. CryptoLocker is one of the most famous ransomware. It spreads through email attachments capable of earning millions of dollars. WinLock is another example, that restricts access to computers.
To conclude
Digital fraud and extortion do not impact a large percentage of people. However, those who fall, victim, have been witnessing a major issue. With the emergence of new technology, the possibilities of fraudulence through the internet are increasing day by day. Cybercrime is on the apex and scams are always ready to entrap you. I have given you a great deal of information that would enrich you to be aware of the present situation. Therefore, if you want to safeguard your business and yourself, it is always important to arm yourself with the necessary shield.
Header image source: https://bit.ly/2QcUhXS

 Ecommerce Development
Ecommerce Development